Verification IP
An RTL processor implementation can be verified using our co-simulation approaches, which compares the implementation with a functional reference model. As a functional reference model, an instruction set simulator (ISS) that is part of the open-source RISC-V VP can be used. Our cross-level processor verification approach generates endless instruction streams and tightly integrates the ISS with the RTL core with the aid of in-memory communication. The setup allows restriction-free instruction generation, enabling a comprehensive testing approach.
SymEx-VP
SymEx-VP focuses explicitly on testing software for constrained embedded devices (e.g. as used in the Internet of Things). This software often interacts very closely with low-level hardware peripherals and in order to support these interactions, during simulation-based software testing, SymEx-VP supports SystemC peripheral models. SystemC is a C++ class library for modeling hardware peripherals.
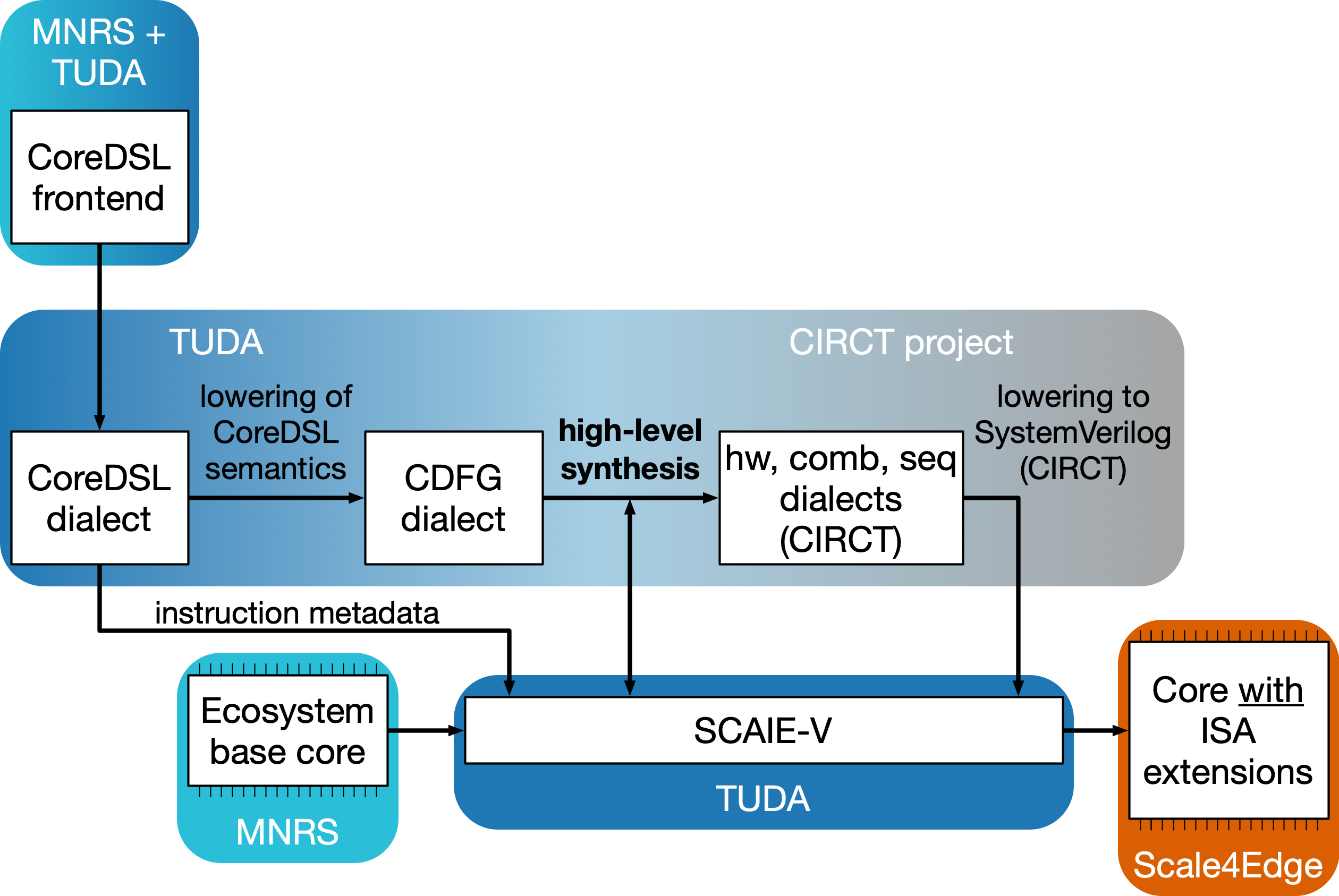
Hardware Architectures and EDA Tools for Creating and Integrating RISC-V ISA Extensions (ISAX Tools)
Instruction Set Architecture eXtensions (here abbreviated as ISAX), sometimes also known as Custom Instructions, are one of the key means to specialize a processor for a specific application domain. They enable, e.g., higher performance or better energy efficiency than realizing the applications using just the generic, general-purpose instruction set.
In Scale4Edge, TUDA works on three key technologies aiming to ease the development and deployment of ISAX:
SCAIE-V and CoreDSL have been open-sourced under a permissive license. Longnail remains proprietary to enable commercial exploitation after the end of Scale4Edge Phase 2.
Extensible Compiler (X-LLVM, Seal5)
The Extensible Compiler provides an LLVM-based toolchain to develop C/C++/Assembly programs for RISC-V. It is designed to easily accommodate custom extensions to the RISC-V ISA by supporting the Scale4Edge developed CoreDSL for describing ISA extensions.
Apache License 2.0
A permissive license whose main conditions require preservation of copyright and license notices. Contributors provide an express grant of patent rights. Licensed works, modifications, and larger works may be distributed under different terms and without source code.
aiT and StackAnalyzer for RISC-V
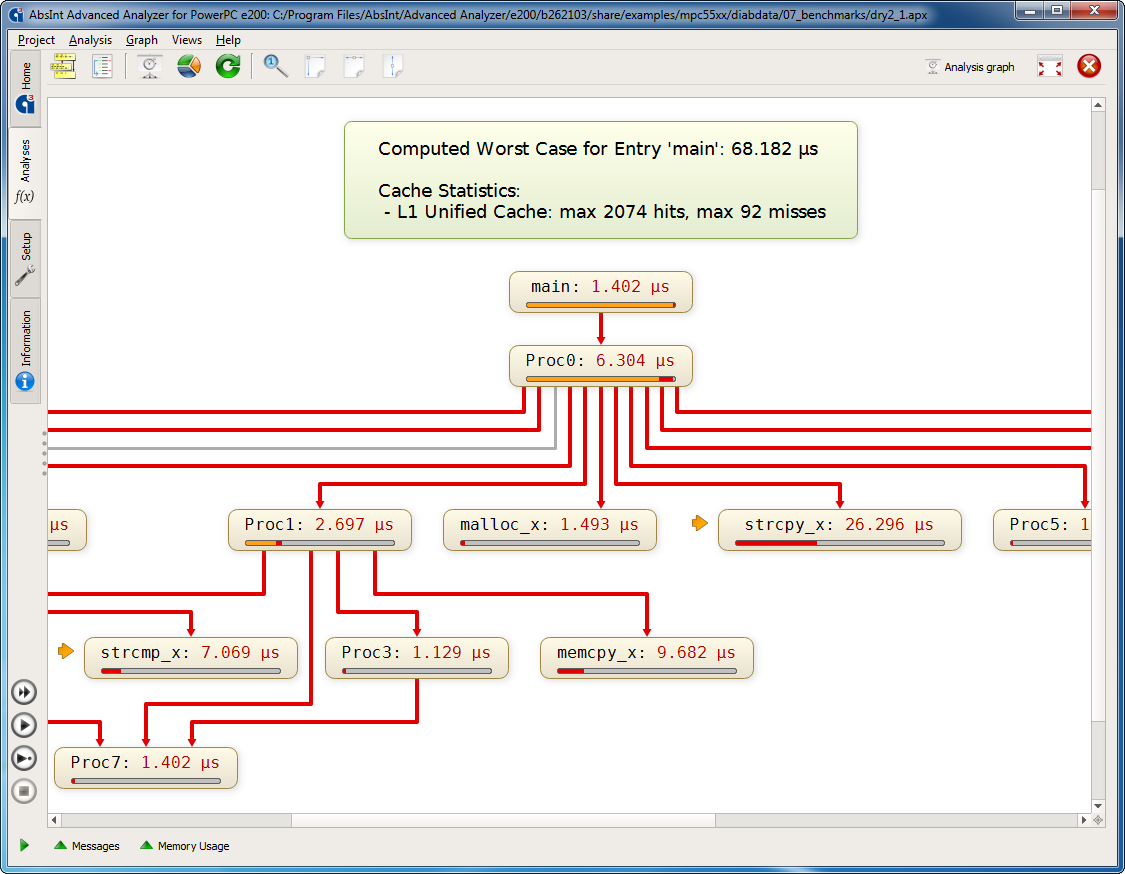
aiT automatically computes safe bounds for the worst-case execution time of tasks in binary executables, taking into account the cache and pipeline behavior of the processor in question.
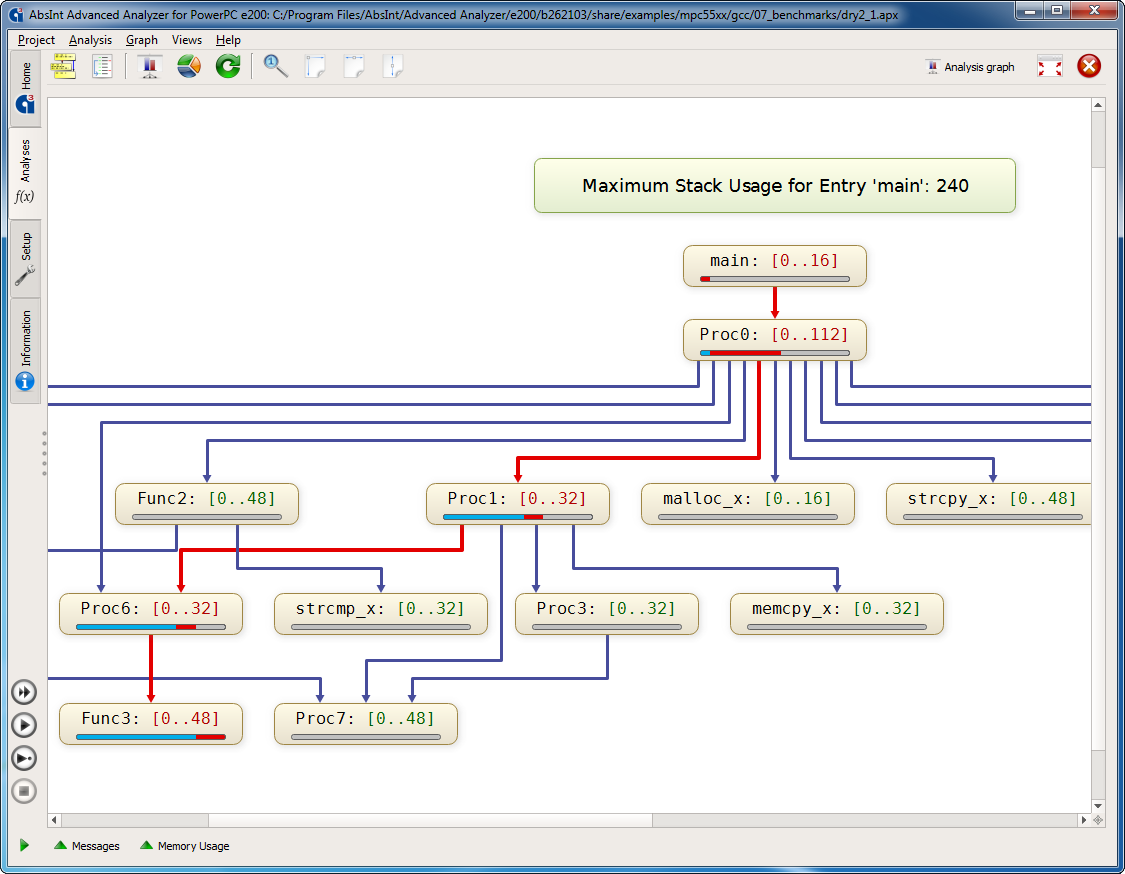
StackAnalyzer automatically determines the worst-case stack usage of the tasks in embedded applications. It directly analyzes binary executables and considers all possible execution scenarios.
This distribution of aiT and StackAnalyzer can be used for evaluation and research within the Scale4Edge project, but not for commercial purposes (see also the license information in the installation packages). Evaluation licenses and commercial licenses can be obtained from AbsInt.